Is it safe to place sensitive information into Intune scripts?
How to get deployed Intune scripts content as an ordinary user
Problem
If you ever asked yourself: "is it safe to place sensitive information into Intune scripts"? I have an answer for you and the answer is DEFINITELY NOT!
Why? Because ordinary users can easily get deployed scripts content 🙂.
How? For example, using my PowerShell functions which I am going to talk about in this post.
Do the users need administrator rights? It depends. For remediation scripts and scripts used when Win32Apps are deployed, no. For non-remediation PowerShell scripts, kind of.
Do the users need any access to the Intune portal or Graph API? No. All data are gathered directly from the client's computer.
How to get Intune remediation scripts content as any user
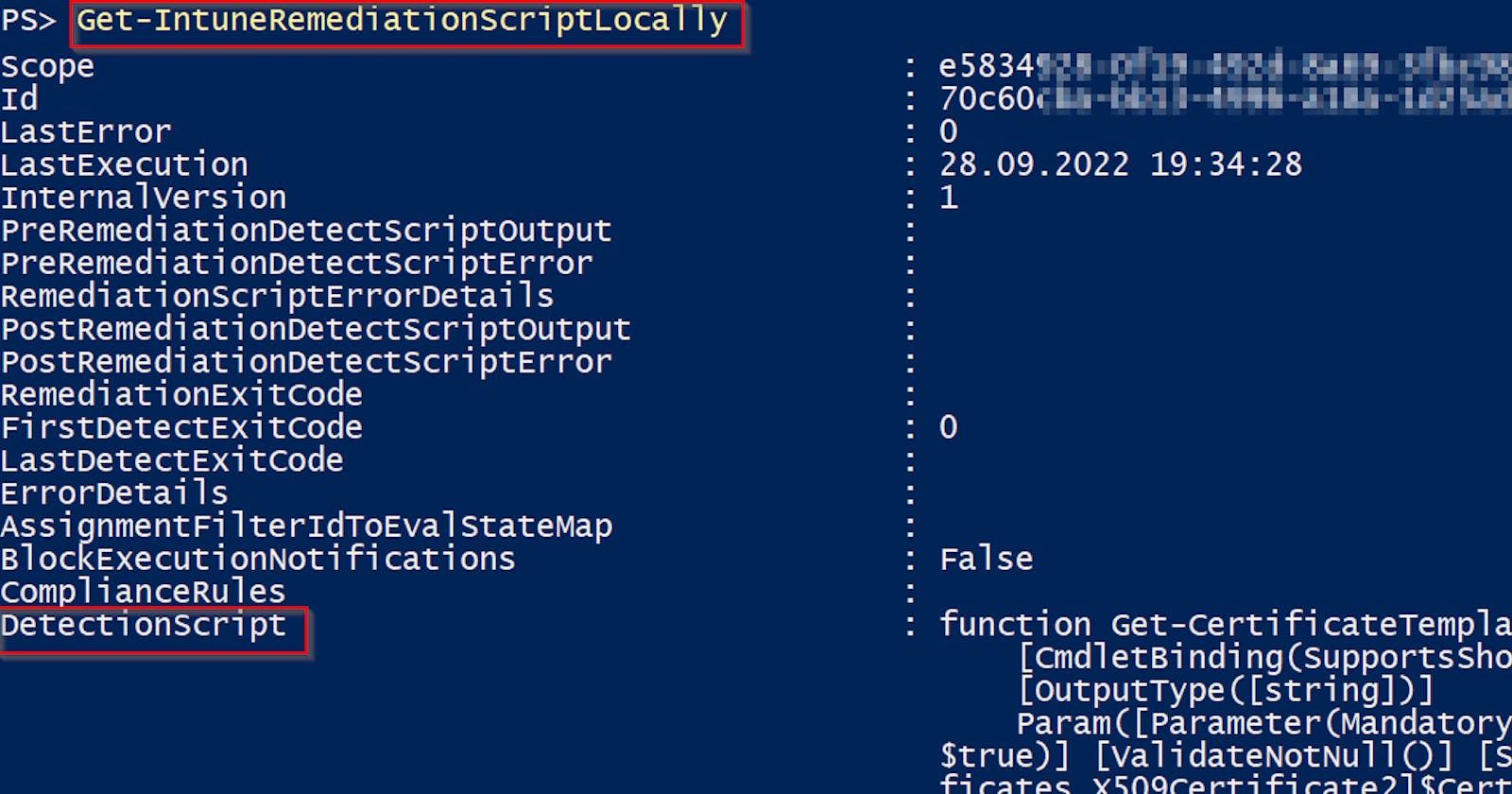
Run function Get-IntuneRemediationScriptLocally from my IntuneStuff module on any Windows computer managed by Intune 👇
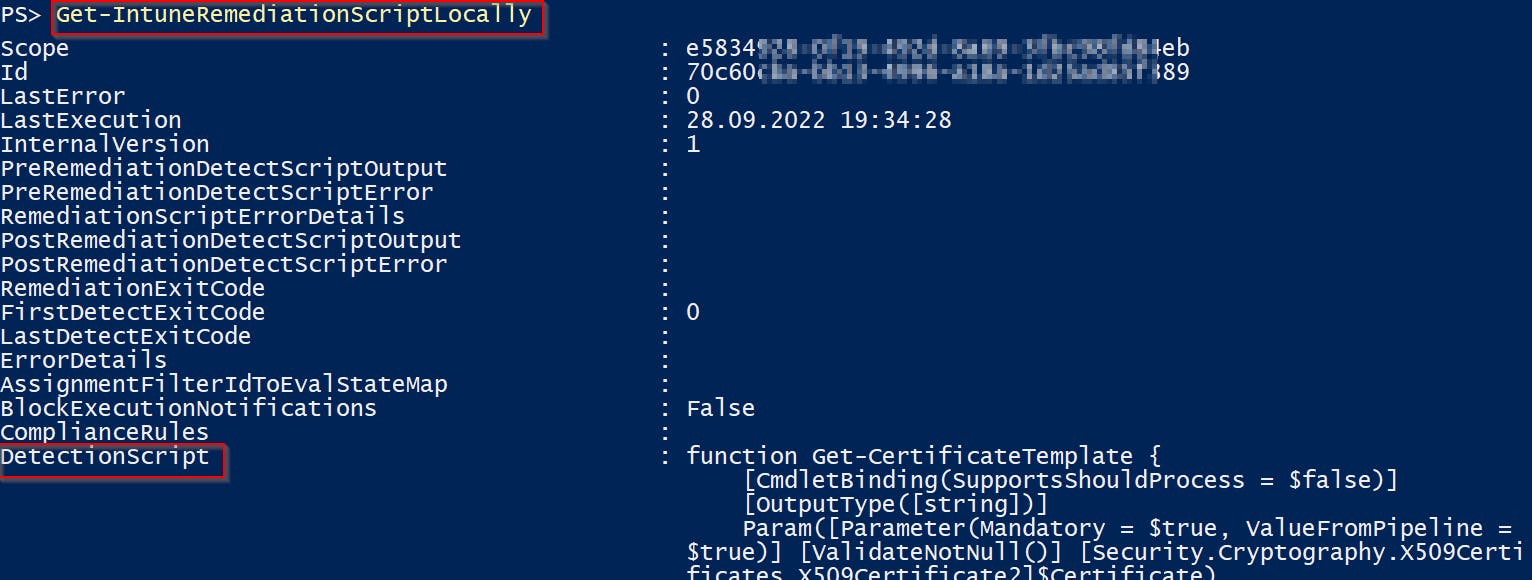
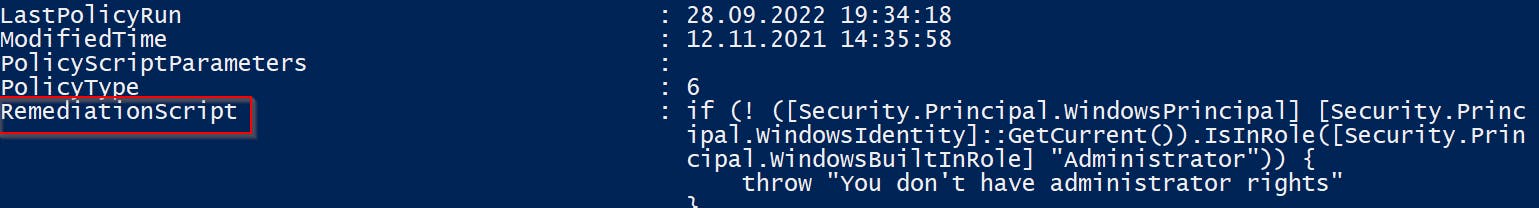
And you will get all deployed remediation scripts including their detection and remediation scripts content 🙂
Remediation scripts are saved as base64 encoded strings in the client's Intune IntuneManagementExtension.log file
How to get Intune non-remediation scripts content as any user
Run function Get-IntuneScriptLocally from my IntuneStuff module on any Windows computer managed by Intune 👇
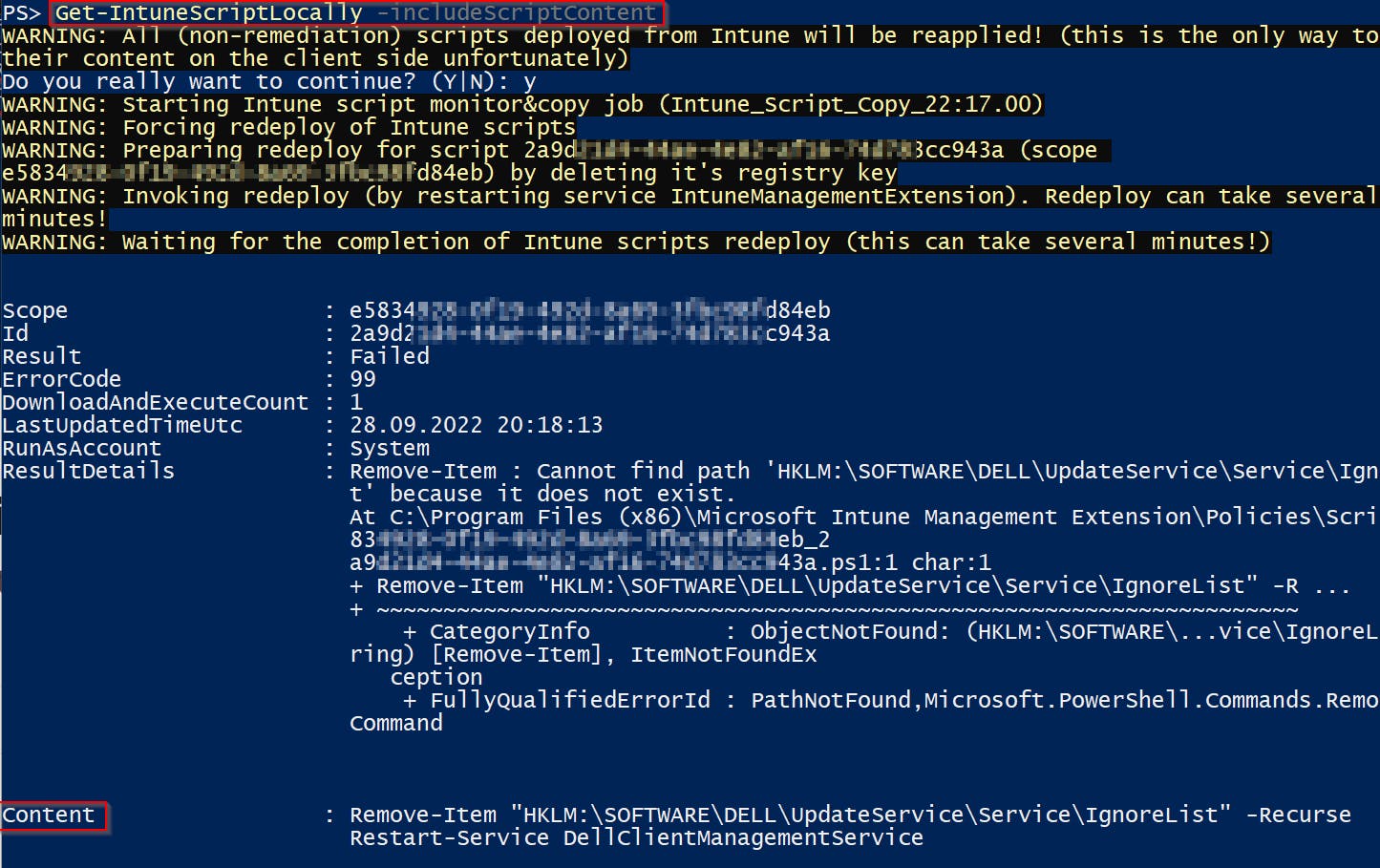
And you will get all deployed non-remediation scripts including scripts content and result 🙂
Non-remediation scripts are saved on the client just during their processing time. Therefore to capture these scripts you have two options:
- a) wait for background refresh (but this can take hours and captures just recurring or new scripts)
- b) run this function as an administrator so it can force redeploy of all scripts (more about this at Force redeploy of intune scripts post). The caveat is obviously that redeploy part, because all scripts get reapplied!
Btw to be able to watch for folder content changes I've created Invoke-FileSystemWatcher function. And for monitoring Intune log file content Invoke-FileContentWatcher. Both are part of CommonStuff module.
How to get Intune Win32App scripts content as any user
Run function Get-IntuneWin32AppLocally from my IntuneStuff module on any Windows computer managed by Intune 👇
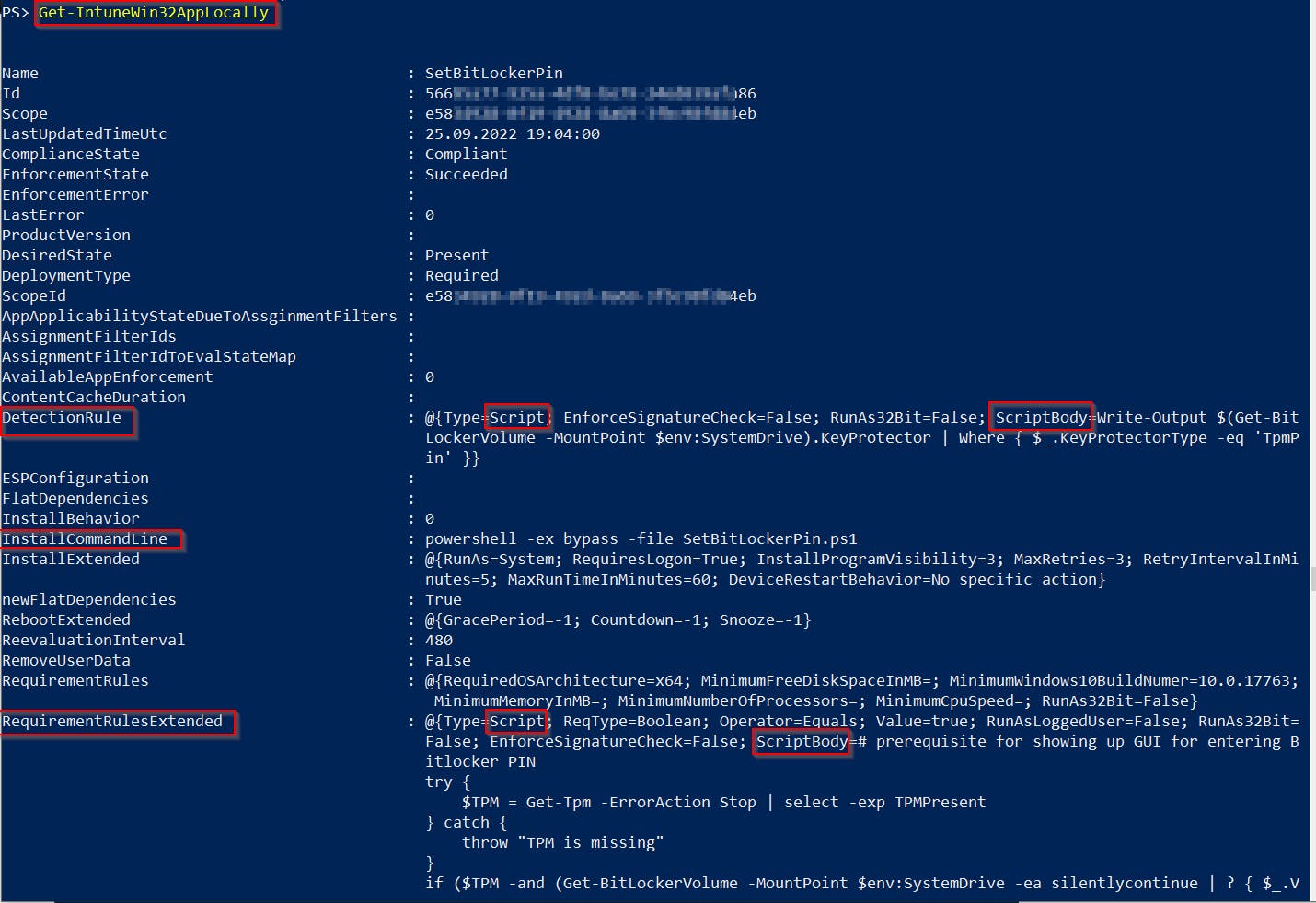
And you will get all deployed Win32Apps including their install/uninstall command and detection/requirement scripts content 🙂
These details are saved in the client's Intune IntuneManagementExtension.log file
Summary
Now you have proof that it is not a good idea to put sensitive information into your Intune scripts 🙏. Moreover, you can use my functions (Get-IntuneRemediationScriptLocally, Get-IntuneScriptLocally, Get-IntuneWin32AppLocally) for reporting/debugging purposes because a lot of useful data are shown.
PS: I've integrated these functions to my RSOP for Intune function too 👍