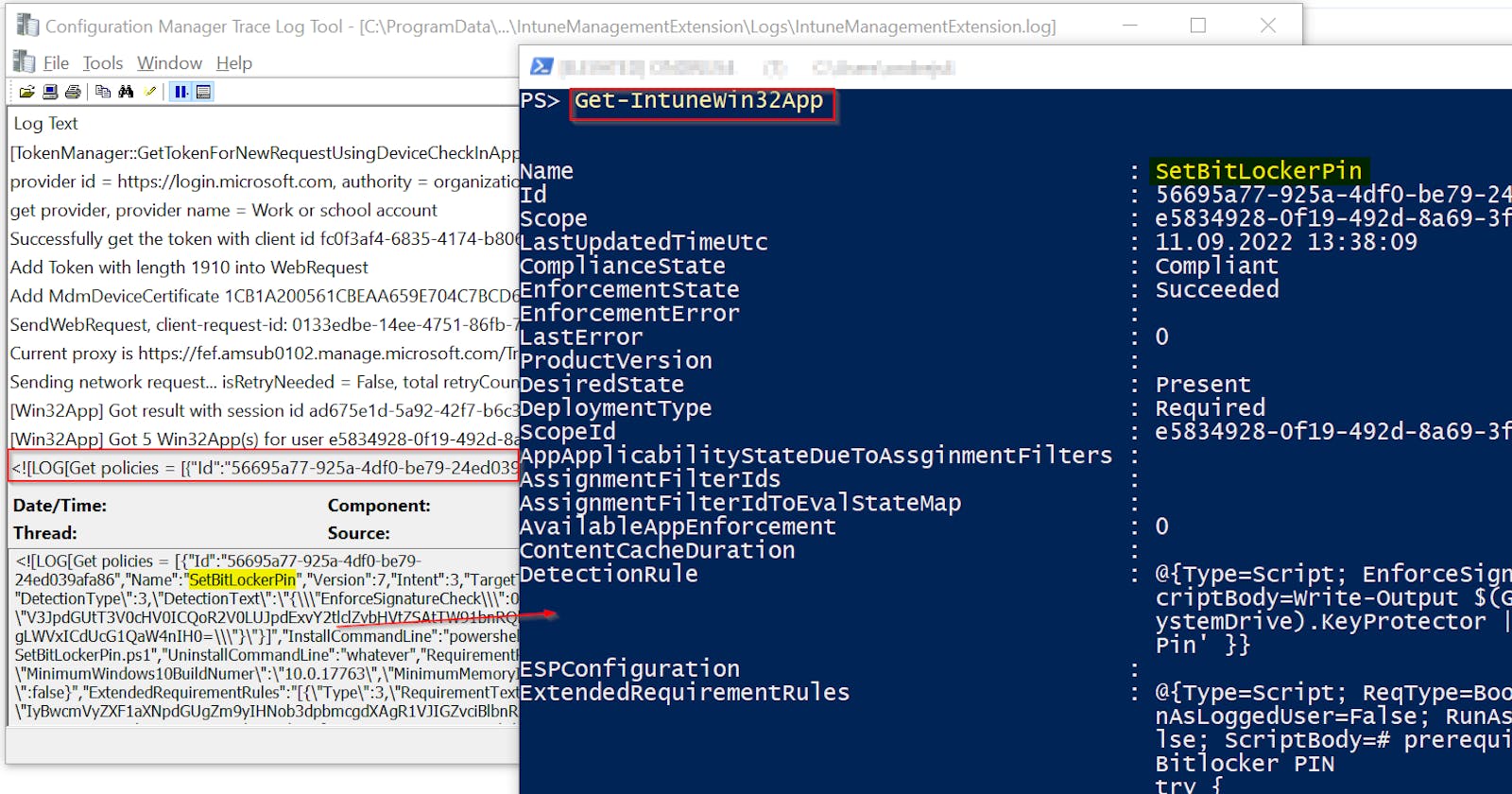
Getting Intune Win32App details from the client's Intune log and registry
Get the local client's Win32App deployment data
28.9.2022 I've rename the function Get-IntuneWin32App to Get-IntuneWin32AppLocally to emphasize that data are gathered locally and to avoid naming conflicts
Problem
If you've ever deployed Win32App through Intune and had some issues with it, you were probably missing some tool that would show you the app deployment status retrieved directly from the local client's data.
Why? Because you probably needed answers to some of these questions:
- What Win32Apps are deployed to this client?
- Did the client really use the newest version of the deployment policy or thanks to some cloud latency etc it just keeps deploying some older one?
- What is the reason for failed app deployment?
- Was the installation successful or did it fail? And if so with what code/error message?
- With what properties was the app deployed?
- What installation/uninstallation command was used?
- What script was used for detection/requirement check?
- ...
Today I will show you my solution to these questions and hopefully make your day 🙂.
Solution
Install IntuneStuff module from PowerShell Gallery and run the Get-IntuneWin32AppLocally function like this 👇
Install-Module IntuneStuff -Force
# show Win32App data (source will be client Intune log file combined with registry data)
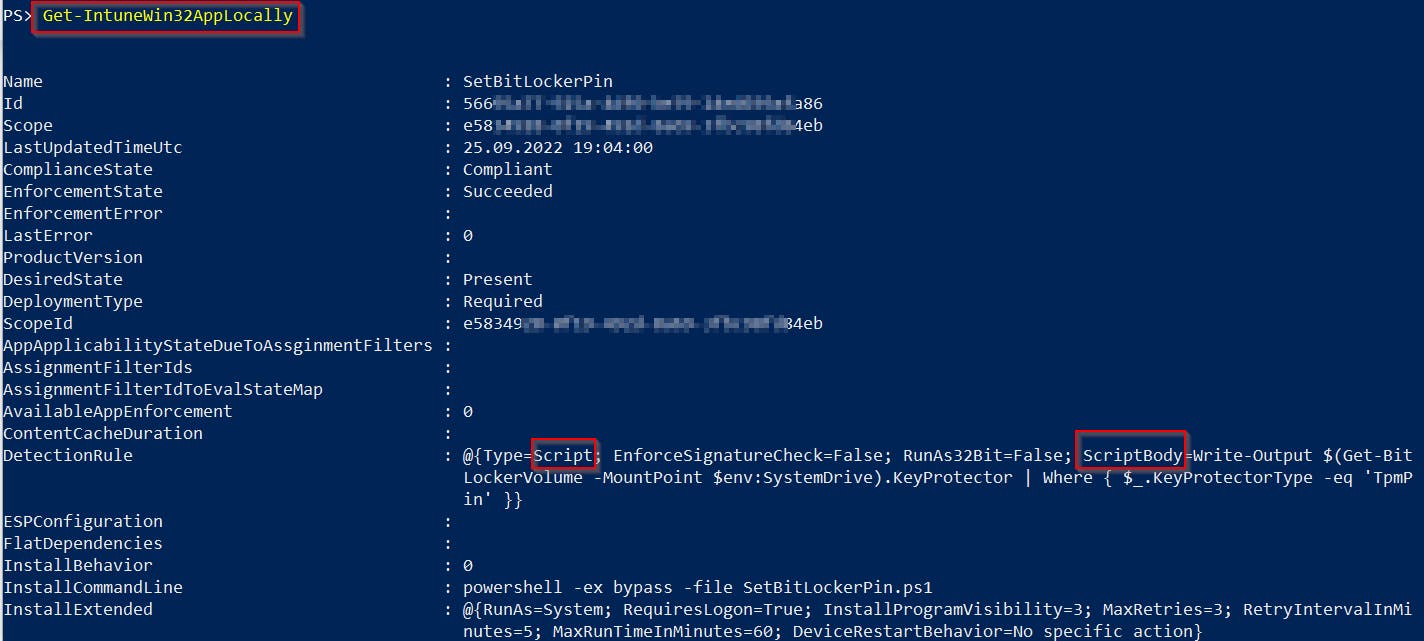
Get-IntuneWin32AppLocally
# show Win32App data (source will be just client Intune log file)
Get-IntuneLogWin32AppData
Get-IntuneLogWin32AppReportingResultData
And you will get results like this 👇
Or you can pipe the results to Out-GridView to show them in the GUI 👇
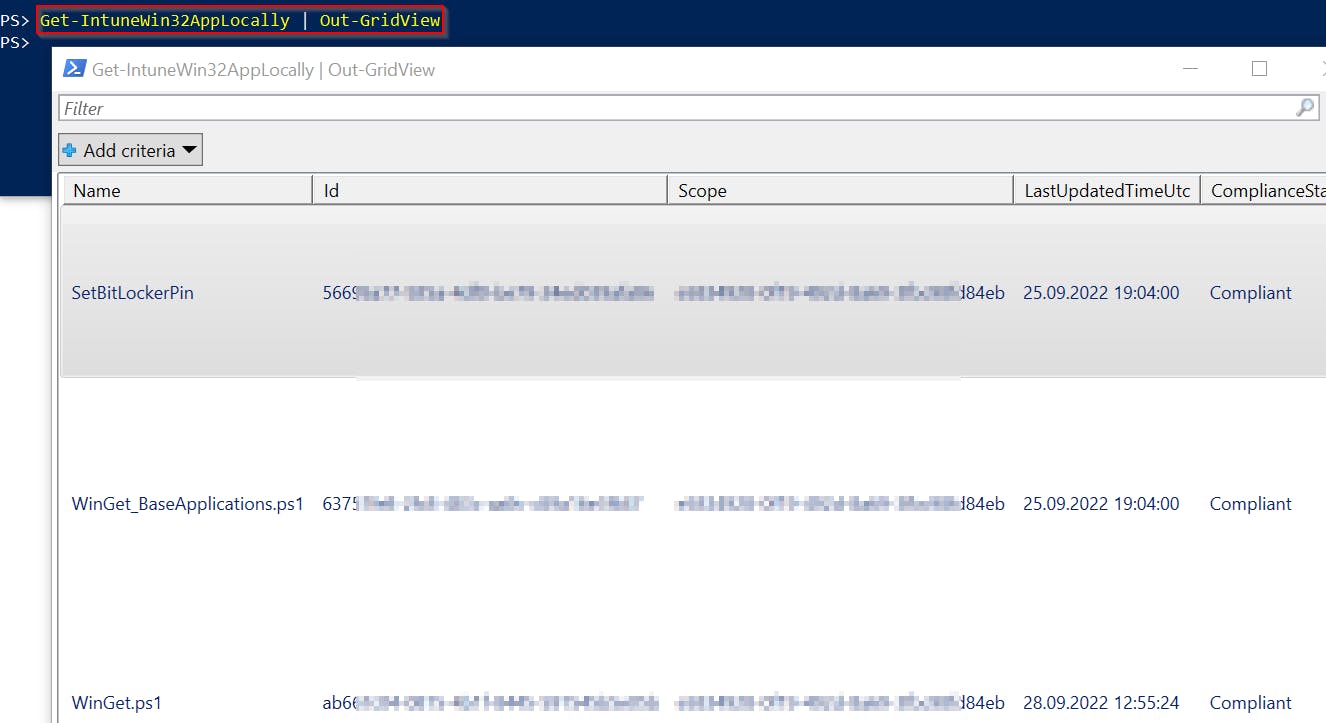
Some data can get truncated when using
Out-GridView!
Benefits of my solution
- no need to authenticate to the Intune (any user can run this)
- data is gathered directly from the client and therefore is 100% recent
- easier than manually checking Intune logs
- the result is a PowerShell object with all relevant data
- detection/remediation script content is also part of the output
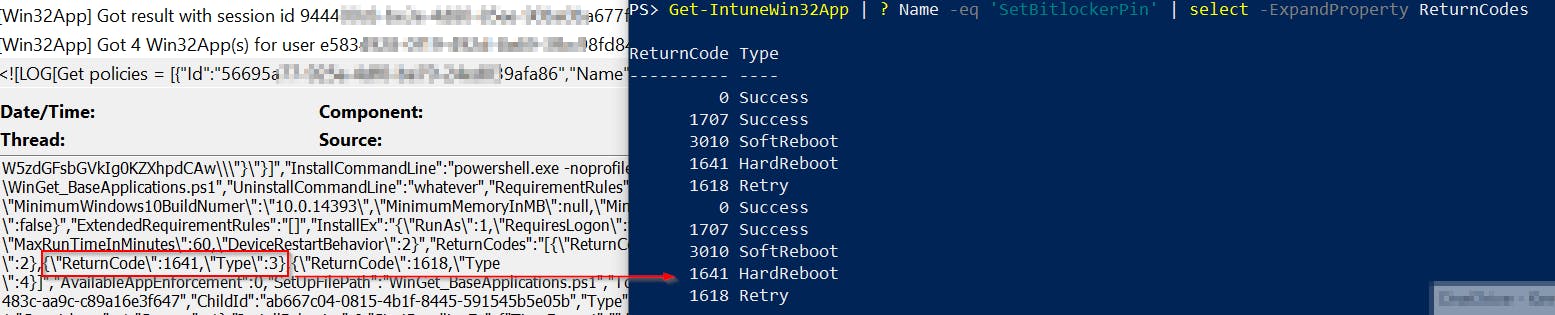
- most of the number codes you can find in Intune log are translated to text message
Where I get these data?
Intune Log
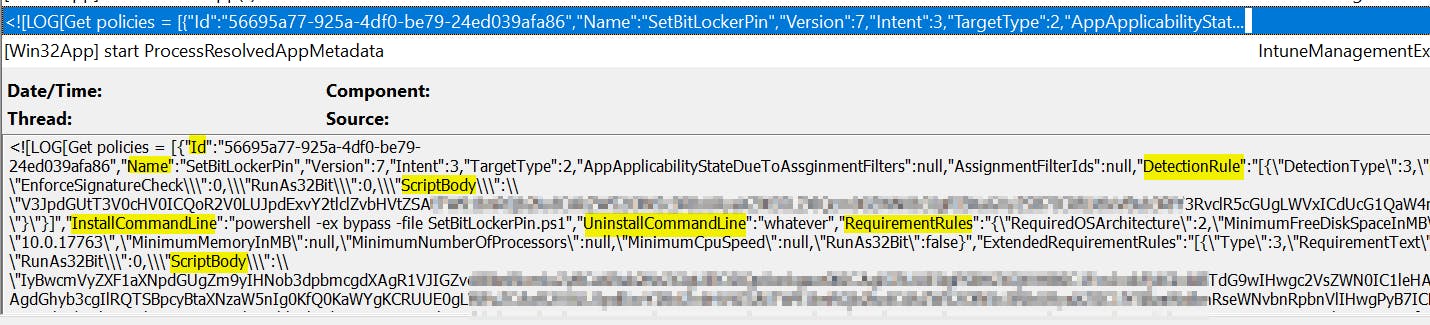
The IntuneManagementExtension.log (C:\ProgramData\Microsoft\IntuneManagementExtension\Logs) contains all relevant data about the processing of Win32Apps. But it can be a little bit hard to find the right information in it. For example processing of Win32Apps is stored in one super long line that looks like this 👇
 This line contains multiple JSONs (one for each app) with details like App Id, Name, Compliance state, Detection and Requirement rules, etc. Helper function
This line contains multiple JSONs (one for each app) with details like App Id, Name, Compliance state, Detection and Requirement rules, etc. Helper function Get-IntuneLogWin32AppData extracts this data and converts them into a PS object using small regex magic and Convert-FromJson cmdlet.
Mentioned JSON contains also ScriptBody property with base64 encoded detection/remediation PS script which can be (and is) easily converted into original PowerShell code.
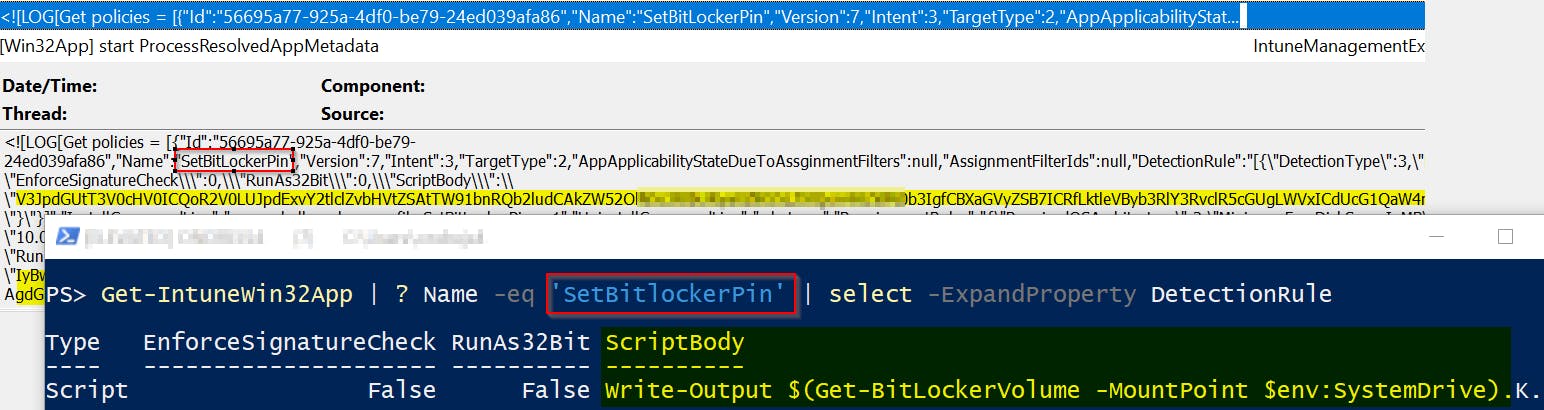
Last but not least most of the number codes are being translated into corresponding text messages. Unfortunately, I wasn't able to find all relevant data so some codes remain intact.
TIP: for Windows errors code translation I use:
[ComponentModel.Win32Exception]<errorCode>
Registry
Another useful data source is the system registry key HKLM:\SOFTWARE\Microsoft\IntuneManagementExtension\Win32Apps. This key includes all deployed apps and details like compliance state, error codes, etc. And it is a lot easier to get compliance and enforcement data from here instead of a log file.

By deleting a specific key, you can force redeploy of the app (more about this topic here).
But It seems like the registry doesn't show apps that don't meet requirement checks! Such apps are in the Intune log and can be easily extracted using another helper function Get-IntuneLogWin32AppReportingResultData.